CyberSafe by InventivTechnology
Complete IT CyberSecurity Services
Security is constantly changing. New rules and regulations seem like a daily occurrence, which makes sense when you consider that cyber criminals are always looking for new ways to steal your data or cause chaos.
A truly secure business is one that quickly responds to new threats, and Inventiv Technology will develop a security plan that keeps your most sensitive data safe. Through careful planning, a common-sense approach, cloud security, and responsive monitoring, we will make sure your security software is up to date, your data is encrypted and stored securely, and that your communications are secure and reliable. Learn more about us and get the IT support and resources you need.

*To learn more, visit us at www.inventivcybersafe.com
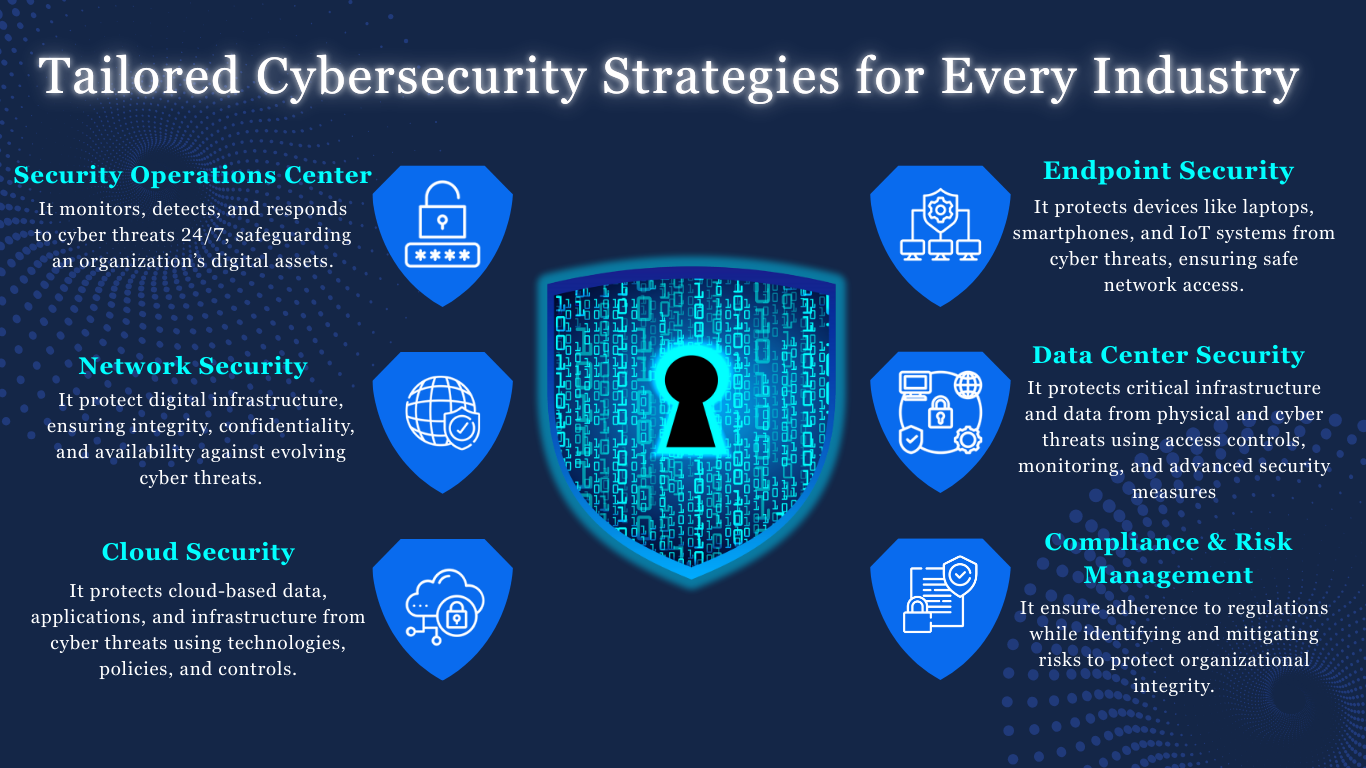
Our procedures are proven and comprehensive:
Asset Management
We work to validate and track all of your assets across your entire enterprise.
Continuous Compliance Management
We identify risks and verify you are in compliance with industry standards, including HIPAA, PCI DSS, ISO 27001, GDPR, and DFARS.
Email Phishing Simulations
It’s important for your employees to be exposed to how cyber-crime works without putting your network at risk. Email phishing simulations test employees on how they would respond to real-life phishing attacks. We’ll track which employees have clicked on a phishing email, who has given away their password, and who has ignored the email.
Endpoint Security
We remotely analyze the security of endpoints connected to the network and outside the network. This includes monitoring endpoint devices and analyzing hardware and software configurations.
File Integrity Monitoring
Our FIM solution detects changes to files and directories effectively in near real time and triggers events based on specific criteria. These events are monitored 24/7 to ascertain if there is any malicious or suspicious activity.
Policy Creation or Revision
Documentation is a key element to any effective security strategy, and we will help you develop new policies, revise existing language, and make sure any documentation is available for the people who need to use it.
Remote Monitoring and Alerts
We track and analyze behaviors, patterns, and security trends on your network, then alert you when needed to keep your network safe.
Cybersecurity Risk Management
We give you and your third-party vendor a risk assessment to understand the risk posture of all the assets, policies, processes, and security controls. Then we analyze the risk identified and apply security control to reduce the risk.
Vulnerability Assessments
We conduct regular vulnerability scans and penetration tests and make recommendations based on the analysis of the reports.
Vulnerability Testing and Assessments
Proactive. Accurate. Risk Adverse.
Proactive. Accurate. Risk Adverse.
Cybersecurity vulnerability testing is a crucial process that involves identifying, analyzing, and addressing security weaknesses in an organization's systems, networks, and applications. By simulating cyber attacks, vulnerability testing helps uncover potential entry points that malicious actors could exploit. Protect your business from data breaches and unauthorized access with Inventiv Technology's comprehensive cybersecurity solutions. Our advanced vulnerability assessment tools and procedures identify and mitigate security risks, ensuring robust protection for your digital assets. Stay ahead of cyber threats with proactive security measures designed to safeguard your sensitive data and maintain compliance with industry standards.

How Do Vulnerability Assessments Help Your Business?
In order to thoroughly secure your networks, you must periodically assess them for security risks and identify cybersecurity vulnerabilities. These network vulnerability assessments explore a wide range of issues across your entire business, and they take servers, networks, systems, hardware, applications, and other elements to get a true picture of where your vulnerabilities lie.This is a systematic process, and at Inventiv Technology,Technologies we leave nothing out:
Testing
Analysis
Risk Assessment
Here we prioritize vulnerabilities according to what systems are affected, data that may be at risk, the severity of a possible attack, and potential damage.
Remediation
Establish Solid Security
Systematic Reviews for Better Security
A Full Spectrum of IT Solutions
Cyber Security Compliance Services
Ensure Security and IT Compliance for Your Business
Regardless of size or industry, a company that can’t keep its sensitive data safe won’t find themselves in business for long. And with cybercriminals as likely to target a small company of 20 employees as they are a global enterprise, no one is exempt. However, most prominent companies have the resources to invest heavily in cyber solutions and can police themselves when they have to comply with industry regulations.
Small and medium businesses have their own advantages though, which come in the form of IT providers like Inventiv Technology. We know what it takes to build a firm security platform that excels in risk management and takes all of your operations into account. Our cybersecurity compliance services ensure all your networks are secure, making compliance an easily attainable goal for your organization.
Align Your Business Goals with Security and Compliance
The Right IT Partnership Is the Key
Cyber Security Compliance Services
Prominent Regulatory Agencies and Requirements
NIST National Institute of Standards and Technology
ISO International Organization for Standardization
HIPAA Health Insurance Portability and Accountability Act
PCI-DSS Payment Card Industry Data Security Standard
GDPR General Data Protection Regulation
AICPA American Institute of Certified Public Accountants
COBIT Control Objectives for Information & Related Technologies

Maintain Security and Compliance Requirements
Just because your network security is compliant doesn’t mean it’s completely secure. This is a common misconception for organizations that follow strict regulations and requirements. The reality is that regulations are reactionary in nature. A new method breaches an insecure organization, records are lost or stolen, and these agencies are left to pick up the pieces and revise their requirements. This means they are always slightly behind the curve.
At Inventiv Technology, we’re always up to date on the latest regulatory requirements for any industry. By ensuring compliance among specific sectors, our cybersecurity compliance services can navigate cyberthreats, prevent data breaches, and assure the best possible results for your business.
We Know the Requirements
It’s not easy to comply with multiple compliance frameworks and regulations. Many of them overlap or contradict each other. Knowledge is critical, and when our clients need us to unravel complicated requirements, we arrive armed with up-to-date knowledge and support.
We Know How to Combine Compliance and Security
We never use compliance as a sole benchmark. Instead, we rely on our own assessments to identify vulnerabilities and risks. Armed with this information, we implement cybersecurity compliance services to develop a security program tailored uniquely to your business, ensuring your safety and compliance.
A Full Spectrum of IT Solutions
Technology is so important to your business that an on-call IT professional is a tremendous asset.
Network and Endpoint Security
Secure End Users. Network Monitoring. Comprehensive Security.
We remotely analyze the security of endpoints connected to the network and monitor the network itself to eliminate all threats.
Persistent Protection Is Key to Network and Endpoint Security
Security for networks and endpoints should be approached together as part of a layered cybersecurity strategy designed to protect your users, shield your network from threats, and establish a security posture that is tough to crack. Security is all about assessing risk and developing a strategy that mitigates or eliminates this risk through technology, procedures, and user education.
At Inventiv Technology, we take network and endpoint security seriously. Cyber threats will never go away, and with more users working remotely or using their personal devices for work purposes, network and endpoint security is critical.
To track security-related issues, we monitor events or changes on your network and wireless devices, analyze hardware and software settings, assess vulnerabilities, and analyze network traffic. It’s critical to know the status and identity of all users and devices in order to prevent an attack. By filtering and monitoring web traffic through our network security solution, we can fine-tune and enforce web access policies and even stop threats before they infiltrate the network and reach endpoints.
Protect Your Network Against Known and Unknown Threats
We incorporate a layered security approach to your entire network for maximum effectiveness.
Full Endpoint Security Protection
Laptops, desktops, mobile phones, tablets, servers, virtual environments, and even printers are devices that are directly interacted with by users. These are called endpoints, and their security is nothing to take for granted. Cyber criminals are always looking for new ways to infiltrate networks, and endpoints are a frequent target. Keeping your endpoints secure can mean installing security software on a central server as well as locally on the device itself. Endpoint security includes:
- Data loss prevention
- Application controls
- Data classification
- Network access controls
- User controls
- Email encryption
We remotely analyze the security of endpoints connected to the network and outside the network; this includes monitoring endpoint devices and analyzing hardware and software configurations.
Gain Complete Computer System Security with Inventiv Technology
Hardware and software are just the beginning of the layered security we provide. Having trained and aware employees is critical to securing an organization, and an effective, ongoing internal security awareness program can help reduce your company’s vulnerability.
Cybersecurity essentials include email phishing simulations, security awareness training, and dark web monitoring. These can help set your employees up with the skills they need to be your business’s first line of defense against online crime.
A Full Spectrum of IT Solutions
Technology is so important to your business that an on-call IT professional is a tremendous asset.
Bolster Your Security Posture with Complete Protection Solutions
Inventiv Technology knows how important it is to keep your critical business data safe and secure. Get in touch with us today, and let our experts help you establish a custom cybersecurity solution.
Network and Endpoint Security
We remotely analyze the security of endpoints connected to the network and outside the network. This includes monitoring endpoint devices and analyzing hardware and software configurations.
Security & Compliance
Our managed security provides 24/7 monitoring with management and review. Our security analysts provide actionable insights to improve your security posture, and they have rapid response identification and reaction to cyber threats.
Bolster Your Security Posture with Complete Protection Solutions
Inventiv Technology knows how important it is to keep your critical business data safe and secure. Get in touch with us today, and let our experts help you establish a custom cybersecurity solution.
Fulfill your vision
At Inventiv Technology, we develop advanced IT solutions that allow your organization to adapt to change, manage growth, and reach your business goals.
Schedule a Complimentary Consultation with Our Experts
Accelerate Your Business Growth and Profitability in Today’s Digitally Transforming Landscape.
- info@inventivtechnology.com
- sales@inventivtechnology.com
- +1 346-630-7010
- Katy, Texas, USA.
